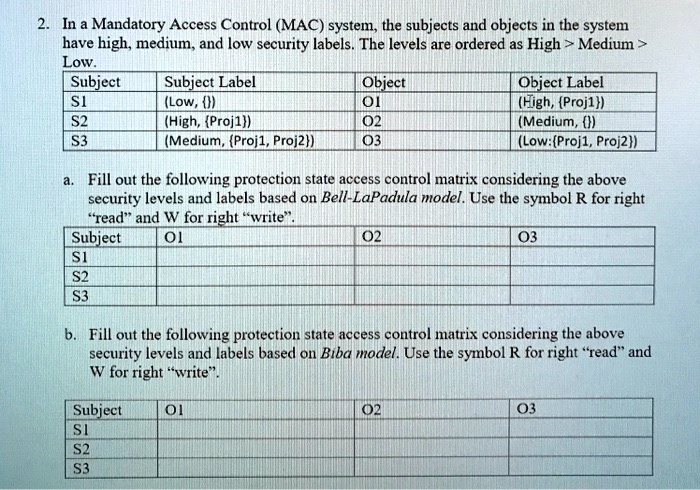
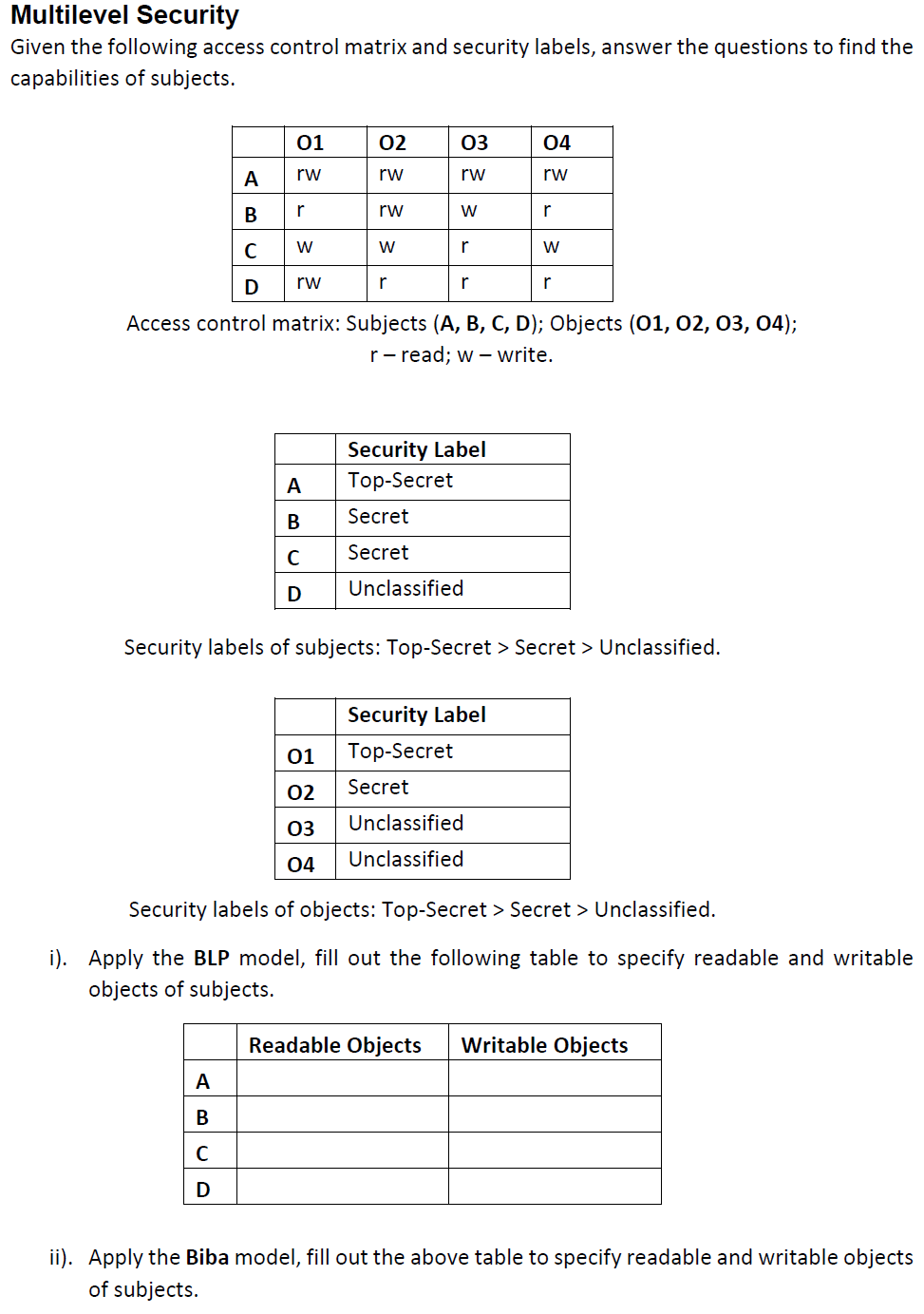
41 security labels access control
Types of Access Control - Rule-Based vs Role-Based & More - Genea An example of role-based access control is if a bank's security system only gives finance managers but not the janitorial staff access to the vault. ... a system administrator configures access policies and defines security permissions. Labels contain two pieces of information—classification (e.g., "top secret") and category (e.g ... Label Security | Oracle Oracle Label Security Control what data users see based on data and session labels. Oracle Label Security records and enforces access permission for data based on project codes, regions, or data classifications. These controls reduce the risk of unauthorized access to sensitive data and help to demonstrate regulatory compliance.
[Knowledge Hub] Windchill PLM Permissions/Access Control/Security Label Article - CS320673 [Knowledge Hub] Windchill PLM Permissions/Access Control/Security Label Modified: 24-Aug-2022 Applies To Windchill PDMLink 10.0 to 12.0 Windchill ProjectLink 10.0 to 12.0 Pro/INTRALINK 8.x + 10.0 to 12.0 Windchill PDM Essentials 10.0 to 12.0 PTC Arbortext Content Manager 10.0 to 12.0 Description How to manage access control?

Security labels access control
PostgreSQL: Documentation: 14: SECURITY LABEL PostgreSQL places no restrictions on whether or how a label provider must interpret security labels; it merely provides a mechanism for storing them. In practice, this facility is intended to allow integration with label-based mandatory access control (MAC) systems such as SELinux. Such systems make all access control decisions based on object ... Security Labels and Access Control - PTC Support Security labels are applied in addition to standard Windchill access control policy and ad hoc rules. A security label acts as a gate; if the user is not ... Label-based access control (LBAC) overview - IBM A security administrator allows users access to protected data by granting them security labels. When a user tries to access protected data, that user's ...
Security labels access control. Access control - Wikipedia In the fields of physical security and information security, access control (AC) is the selective restriction of access to a place or other resource, while access management describes the process.The act of accessing may mean consuming, entering, or using. Permission to access a resource is called authorization.. Locks and login credentials are two analogous mechanisms of access control. Security - FHIR v4.3.0 - Health Level Seven International Two of the classic Access Control models are: Role-Based Access Control (RBAC), and Attribute-Based Access Control (ABAC). In Role-Based Access Control (RBAC), permissions are operations on an object that a user wishes to access. Permissions are grouped into roles. A role characterizes the functions a user can perform. Roles are assigned to users. Setting Access Control Permissions for Agreement Managers - PTC Read permission is required to access any object and view its information page. The following table illustrates additional access control permissions required for actions often completed by an agreement manager. The object location column has the following values. Use these values to determine the domain in which to grant access control ... Contact security - Oracle Contact security, also known as Label-Based Access Control (LBAC), allows you to use labels to manage access to contacts in your database. Note: Contact security is part of the Oracle Eloqua Security Administration Cloud Service and is included in the Standard and Enterprise trims.
How security labels control access - help.hcltechsw.com Security labels rely on security label components to store information about the classification of data and about which users have access authority. Label-based access control (LBAC) works by comparing the labels that you have associated with users against labels that you have associated with data by using a predefined rule set (IDSLBACRULES). LBAC security labels - IBM In label-based access control (LBAC) a security label is a database object that describes a certain set of security criteria. Security labels are applied to ... Mandatory Access Control: How It Works - Firewall Times Mandatory access control relies on a system of security labels. Every resource under MAC has a security classification, such as Classified, Secret, and Top Secret. Likewise, every user has one or more security clearances. To access a given resource, the user must have a clearance matching or exceeding the resource's classification. Introduction to column-level access control | BigQuery ... 2 days ago · Using BigQuery column-level access control, you can create policies that check, at query time, whether a user has proper access. For example, a policy can enforce access checks such as: You must be in group:high-access to see the columns containing TYPE_SSN. To enhance column-level access control, you can optionally use dynamic data masking ...
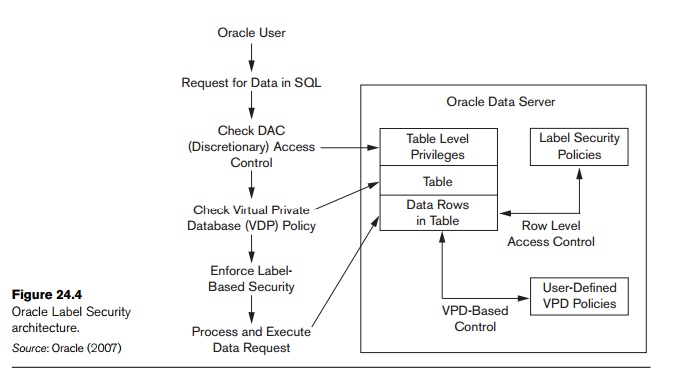
Security label components - IBM The elements of these components are used to define security labels, which control access to protected tables. Security label components represent any ... Oracle Label Security Oracle Label Security uses row level data classifications to enforce access controls restricting users to only the data they are allowed to access. It enables organizations to control their operational and storage costs by enabling data with different levels of sensitivity to co-mingle within the same database. Access Control Models: MAC, DAC, RBAC, & PAM Explained MAC works by applying security labels to resources and individuals. These security labels consist of two elements: Classification and clearance — MAC relies on a classification system (restricted, secret, top-secret, etc.) that describes a resource's sensitivity. Users' security clearances determine what kinds of resources they may access. Security Labels and Mandatory Access Control (MAC) - IBM Mandatory Access Control (MAC) is a security policy that governs which subjects can access which objects, and in what way, based upon certain rules.
Access Control Types and Models - Identity Management Institute® Access Control Types and Models. Blog. Access controls are designed to allow, deny, limit, and revoke access to resources through identification, authentication, and authorization. When we discuss managing access to data, we have to address both physical and logical access. Physical access refers to buildings, devices, and documents while ...
Security-labels - FHIR v4.3.0 - Health Level Seven International A security label is a concept attached to a resource or bundle that provides specific security metadata about the information it is fixed to. The Access Control decision engine uses the security label together with any provenance resources associated with the resource and other metadata (e.g. the resource type, resource contents, etc.) to
Security: Access Control - Bosch Security and Safety Systems I Global When trying to access the Access Easy Controller via Microsoft Edge, Chrome or other web browsers, you may get an error, "the connection for this site is not secure", which prevents you from connecting to the AEC. 441 0 03-30-2022 Can I downgrade my AEC firmware to 2.1.8.5?
Mandatory access control - Wikipedia Access to the labels and control mechanisms are not [citation needed] robustly protected from corruption in protected domain maintained by a kernel. The applications a user runs are combined with the security label at which the user works in the session. Access to information, programs and devices are only weakly controlled [citation needed].
Mandatory Access Control - an overview | ScienceDirect Topics Mandatory Access Control ( MAC) is system-enforced access control based on subject's clearance and object's labels. Subjects and objects have clearances and labels, respectively, such as confidential, secret, and top secret. A subject may access an object only if the subject's clearance is equal to or greater than the object's label.
Database Security Requirements Guide - STIG Viewer The DBMS must associate organization-defined types of security labels having organization-defined security label values with information in transmission. Without the association of security labels to information, there is no basis for the DBMS to make security-related access-control decisions. Security labels are abstractions representing the...
Label-based access control Security labels are objects applied to rows and columns in order to protect these data, and granted to users to give them access to protected data. Protecting tables at row and column levels Protect rows and columns by associating them with security objects by including clauses in the CREATE TABLE and ALTER TABLE statements. Exemptions
8 Access Control Models - Strengths, Weaknesses, and More Which brings us to our next model of access control - read on. Mandatory Access Control (MAC): the Secure Model Under mandatory access control (MAC), security administrators set access labels for both users and objects. Mandatory access control is the most secure of the major access control models, and also the most demanding to maintain.
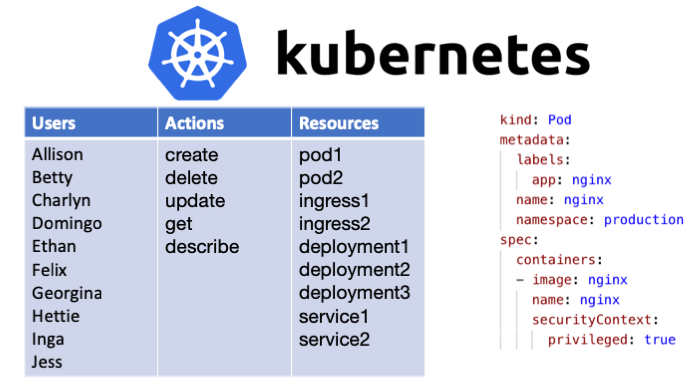
Controlling Access to the Kubernetes API | Kubernetes Jul 09, 2022 · This page provides an overview of controlling access to the Kubernetes API. Users access the Kubernetes API using kubectl, client libraries, or by making REST requests. Both human users and Kubernetes service accounts can be authorized for API access. When a request reaches the API, it goes through several stages, illustrated in the following diagram: Transport security By default, the ...
Kisi Controller Pro 2 helps companies modernise their access ... Sep 07, 2022 · Kisi Inc., the pioneer in cloud-based access control solutions, launches Kisi Controller Pro 2, which will help companies modernise their legacy access control. This cost-effective migration would mean enhanced security and control for companies across a broad range of industries.
Secure external collaboration using sensitivity labels In addition to that, it is possible to make the protected content time-bound as well as control whether users can access it offline and for how long. In this case your label may look like this: Figure 3: A sensitivity label granting Authenticated users view-only access.
inotec Barcode Security - Obermark Importantly, inotec Barcode Security had to make certain that bacteria cannot accumulate under the labels and that the materials used are in line with food regulations. Using the in-mould process, during which labels are injected directly into the plastic of the container, inotec Barcode Security was able to provide a solution to meet these ...
Label-based access control (LBAC) overview - IBM In label-based access control (LBAC) a security label is a database object that describes a certain set of security criteria. Security labels are applied to data in order to protect the data. They are granted to users to allow them to access protected data. Format for security label values

10pcs/lot Disposable Passive RFID UHF clothes barcode label 860-960MHz Custom Printed RFID Clothing Security Labels
ITIL security management - Wikipedia The Control sub-process organizes and manages the security management process. The Control sub-process defines the processes, the allocation of responsibility for the policy statements and the management framework. The security management framework defines the sub-processes for development, implementation and evaluations into action plans.
Using Security Labels for Directory Access and Replication Control - Isode The access control model is that a Security Label is associated with each entry in the directory, and that label indicates the sensitivity of the information contained in the directory entry. The example DIT "organizations", with different Security Labels.
Access control for folders with IAM | Resource Manager ... Sep 28, 2022 · IAM lets you adopt the security principle of least privilege, so you grant only the necessary access to your resources. IAM lets you control who (users) has what access (roles) to which resources by setting IAM policies. IAM policies grant specific role(s) to a user giving the user certain permissions.
Mandatory Access Control: How does it work? - IONOS Oct 14, 2020 · There are a number of options available for implementing and maintaining access control, including Mandatory Access Control. This model is also used in the political and military branches, which require tamper-proof protection of data. Keep reading to find out how this rule-based access control works and what its pros and cons are.
Sensitivity labels for Microsoft Teams - Microsoft Teams Sensitivity labels allow Teams admins to protect and regulate access to sensitive organizational content created during collaboration within teams. After you configure sensitivity labels with their associated policies in the Microsoft Purview compliance portal, these labels can be applied to teams in your organization.
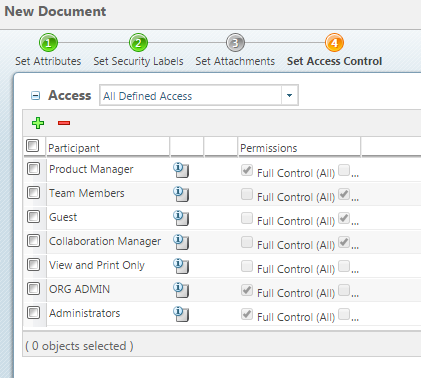
Security Labels Overview - PTC Uniquely configured by each site, security labels work with the Windchill access control policies and ad hoc permissions for an object to determine whether a user is authorized to access an object. A site can configure multiple security labels to cover various needs, such as identifying legal information, establishing export control criteria, or protecting proprietary information.
Access Control Card Customized Printing Rfid Paper Roll Label Rfid Security Label For Acess Control System - Buy Paper Roll Smart Uhf Sticker Tag Label Long Range Rfid Sticker - Buy Rfid Sticker Long ...
Label-Based Access Control - IBM Security labels are objects applied to rows and columns in order to protect these data, and granted to users to give them access to protected data. Protecting ...
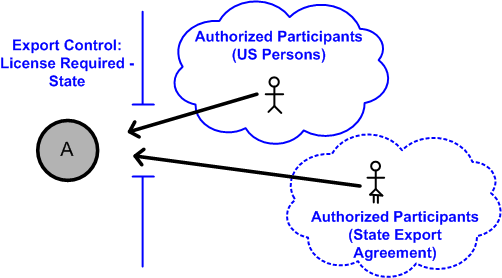
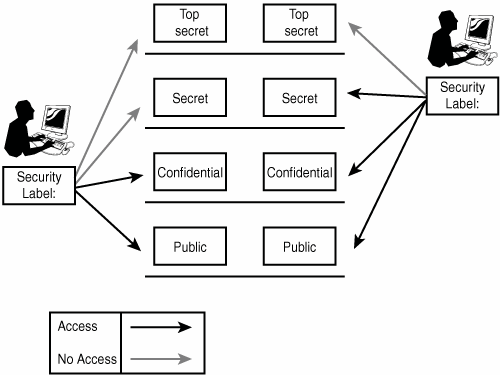
Access Control using Security Labels & Security Clearance Security Labels and Security Clearance provides a mechanism for controlling access to information that works well for large numbers of users. It can be an effective approach for access control in organizations that do not use non-electronic security labels. The following diagram shows the translation of the earlier example into electronic form.
How security labels control access - IBM Security labels rely on security label components to store information about the classification of data and about which users have access authority.
DirectorySecurity Class (System.Security.AccessControl) Examples. The following code example uses the DirectorySecurity class to add and then remove an access control list (ACL) entry from a directory. You must supply a valid user or group account to run this example. using namespace System; using namespace System::IO; using namespace System::Security::AccessControl; // Adds an ACL entry on the specified directory for the // specified account. void ...
Access Control Models - CompTIA Security+ SY0-501 - 4.3 Every object that someone may need to access needs to be assigned a label. It's either confidential, or secret, or top secret, or some other type of label. The users then are provided with certain rights. Certain users can access confidential objects. Other users may be able to access top secret objects.
Label-based access control (LBAC) overview - IBM A security administrator allows users access to protected data by granting them security labels. When a user tries to access protected data, that user's ...
Security Labels and Access Control - PTC Support Security labels are applied in addition to standard Windchill access control policy and ad hoc rules. A security label acts as a gate; if the user is not ...
PostgreSQL: Documentation: 14: SECURITY LABEL PostgreSQL places no restrictions on whether or how a label provider must interpret security labels; it merely provides a mechanism for storing them. In practice, this facility is intended to allow integration with label-based mandatory access control (MAC) systems such as SELinux. Such systems make all access control decisions based on object ...



















![PDF] A System for Supporting The Cyber Security Control of ...](https://d3i71xaburhd42.cloudfront.net/e24f299c73998f565a63fa1258a15c55ab10c816/2-Table1-1.png)




Post a Comment for "41 security labels access control"